



PLEASE ROTATE ME


Telink Staff
August 2, 2024


Explore why IoT and OT security should go hand-in-hand.
Imagine a world where machines and devices in factories, power plants, and critical infrastructure can communicate and operate seamlessly, increase efficiency, and reduce human error. This is the promise of IoT in operational technology (OT) environments. However, with this interconnected future comes a new array of security challenges.
As industries embrace IoT, the global market for the Industrial Internet of Things (IIoT) is projected to grow from $147.2 billion in 2023 to $391.8 billion by 2028, at a compound annual growth rate (CAGR) of 21.6%, according to BCC Research. This means securing OT devices is more crucial than ever, and IoT holds great potential to provide extra protection against future attacks that are growing in complexity.
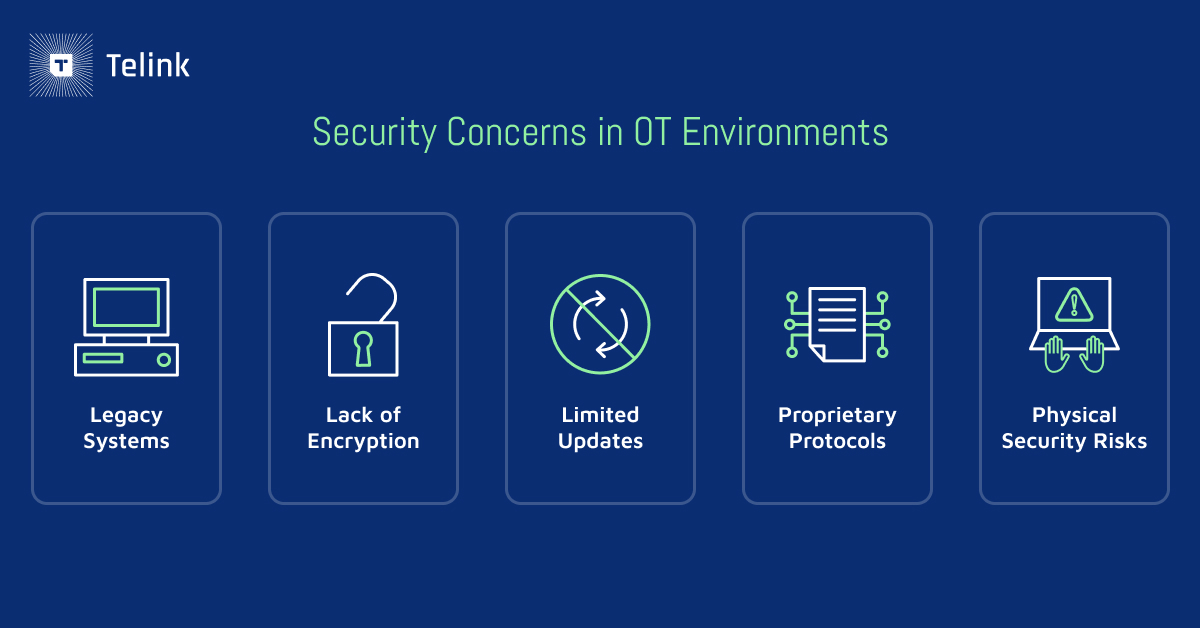
OT environments face several security vulnerabilities and gaps that IoT can help fill. For example, many OT environments rely on legacy systems that are not safeguarded against intelligence systems and advanced technology. These older infrastructures lack modern security features, making them particularly susceptible to today’s attacks. Additionally, communication between these older OT devices often occurs without encryption, leaving sensitive data exposed to potential interception and unauthorized access.
Unlike IoT systems, traditional OT devices may not be updated regularly due to concerns about downtime and operational disruptions, resulting in outdated software that remains vulnerable. Plus, many OT systems often use proprietary communication protocols to support specific operations, which are ultimately challenging to secure and may not be compatible with contemporary security solutions. The physical aspect of OT environments also makes them susceptible to hardware attacks made by unauthorized personnel or ill-motivated employees with access to high-security areas.
If these weaknesses aren’t addressed, they can lead to an array of detrimental threats, including:
With technology, there’s no such thing as being too safe. In fact, it’s always best to be several steps ahead with the latest developments in IoT and OT security.
Transitioning from potential threats to solutions, here’s how IoT technology can enhance OT security:
Offering a more proactive approach to security, IoT uses device connectivity and automation to maintain secure OT systems that would be otherwise challenging to maintain manually.
Simply updating OT devices with IoT capabilities and solutions isn’t enough to keep an entire ecosystem safe. Ensure that your new IoT-fortified OT products work the way they should with these key practices.
Secure communication protocols between IoT and OT devices are necessary to safeguard sensitive data. Protocols like TLS (Transport Layer Security) ensure that data transmitted between devices is encrypted and authenticated, preventing illicit access and data breaches. Also, consider using secure Application Programming Interfaces (APIs) for data exchange so that only authorized applications and devices can communicate while keeping potential interceptors out.
Regular updates and patches for both IoT and OT devices are crucial for mitigating vulnerabilities in software and firmware. Otherwise, hackers can exploit known bugs and security gaps to gain access to these assets. Be cognizant of potential weaknesses and deploy updates to fix them.
IoT devices need to be able to ceaselessly collect real-time data in order to help users detect unusual activity in time. Ensure that your IoT products not only meet this need but seamlessly connect and relay this information to other devices in the same network. As a result, users can expect faster incident response and gain the necessary data and insights to future-proof security measures.
The integration of IoT technology into OT environments offers significant advantages for enhancing security. With Telink, developers can create IoT technologies that support OT systems for a robust IoT and OT security framework that keeps operational technology environments vigilant and resilient. Choosing the latest Telink SoC series, rest assured that your device will be fortified with top-of-the-line security features such as true random number generation, root of trust (RoT), and hardware encryption accelerator, to name a few. Plus, our solutions are designed to be compatible with the industry’s leading IoT protocols like Matter, Zigbee, Thread, and Bluetooth.
Don’t settle for simple — set the foundation for an impenetrable security framework with Telink.
Visit Telink’s wiki to learn more about our development tools, ask us a question through our Technical Forum, or contact us directly today.